Delegations
Theory
Kerberos delegations allow services to access other services on behalf of domain users.
Types of delegation
The "Kerberos" authentication protocol features delegation capabilities described as follows. There are three types of Kerberos delegations
- Unconstrained delegations (KUD): a service can impersonate users on any other service.
- Constrained delegations (KCD): a service can impersonate users on a set of services
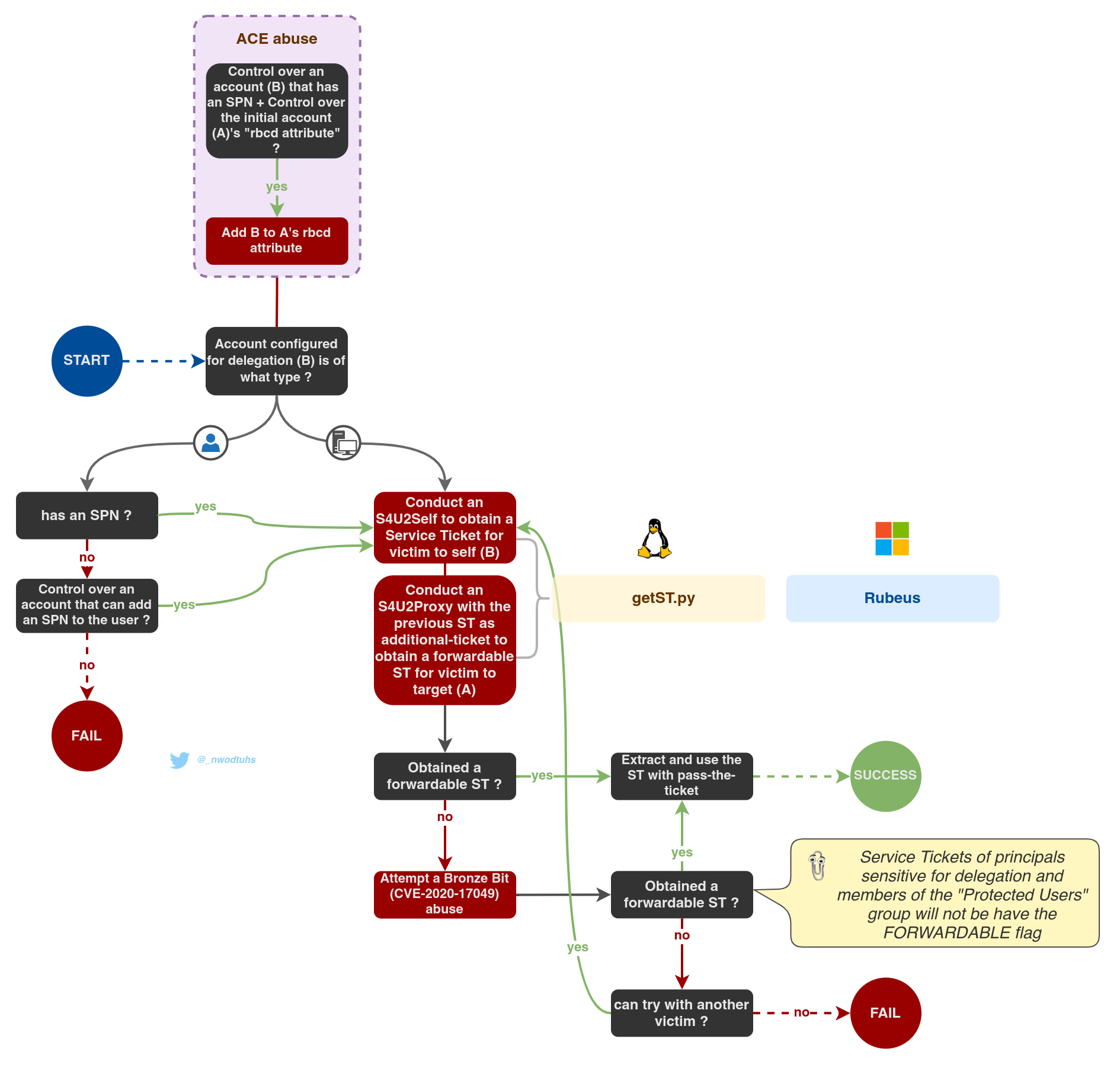
- Resource based constrained delegations (RBCD) : a set of services can impersonate users on a service
With constrained and unconstrained delegations, the delegation attributes are set on the impersonating service (requires SeEnableDelegationPrivilege in the domain) whereas with RBCD, these attributes are set on the target service account itself (requires lower privileges).
Extensions
Kerberos delegations can be abused by attackers to obtain access to valuable assets and sometimes even escalate to domain admin privileges. Regarding constrained delegations and rbcd, those types of delegation rely on Kerberos extensions called Service-for-User (S4U).
Want to know more about S4U2self and S4U2proxy (required to understand some delegation abuses) : click here.
Simply put, Service for User to Self (S4U2self) allows a service to obtain a Service Ticket, on behalf of another user (called "principal"), to itself. Service for User to Proxy (S4U2proxy) allows a service to obtain a Service Ticket, on behalf of a user to a different service.
Some of the following parts allow to obtain modified or crafted Kerberos tickets. Once obtained, these tickets can be used with Pass-the-Ticket.
Practice
Recon
From UNIX-like systems, Impacket's findDelegation (Python) script can be used to find unconstrained, constrained (with or without protocol transition) and rbcd.
findDelegation.py "DOMAIN"/"USER":"PASSWORD"At the time of writing (13th October 2021), a Pull Request is pending to feature a -user filter to list delegations for a specific account.
findDelegation.py -user "account" "DOMAIN"/"USER":"PASSWORD"Abuse
Unconstrained delegations (KUD)
Read the (KUD) Unconstrained article for more insight
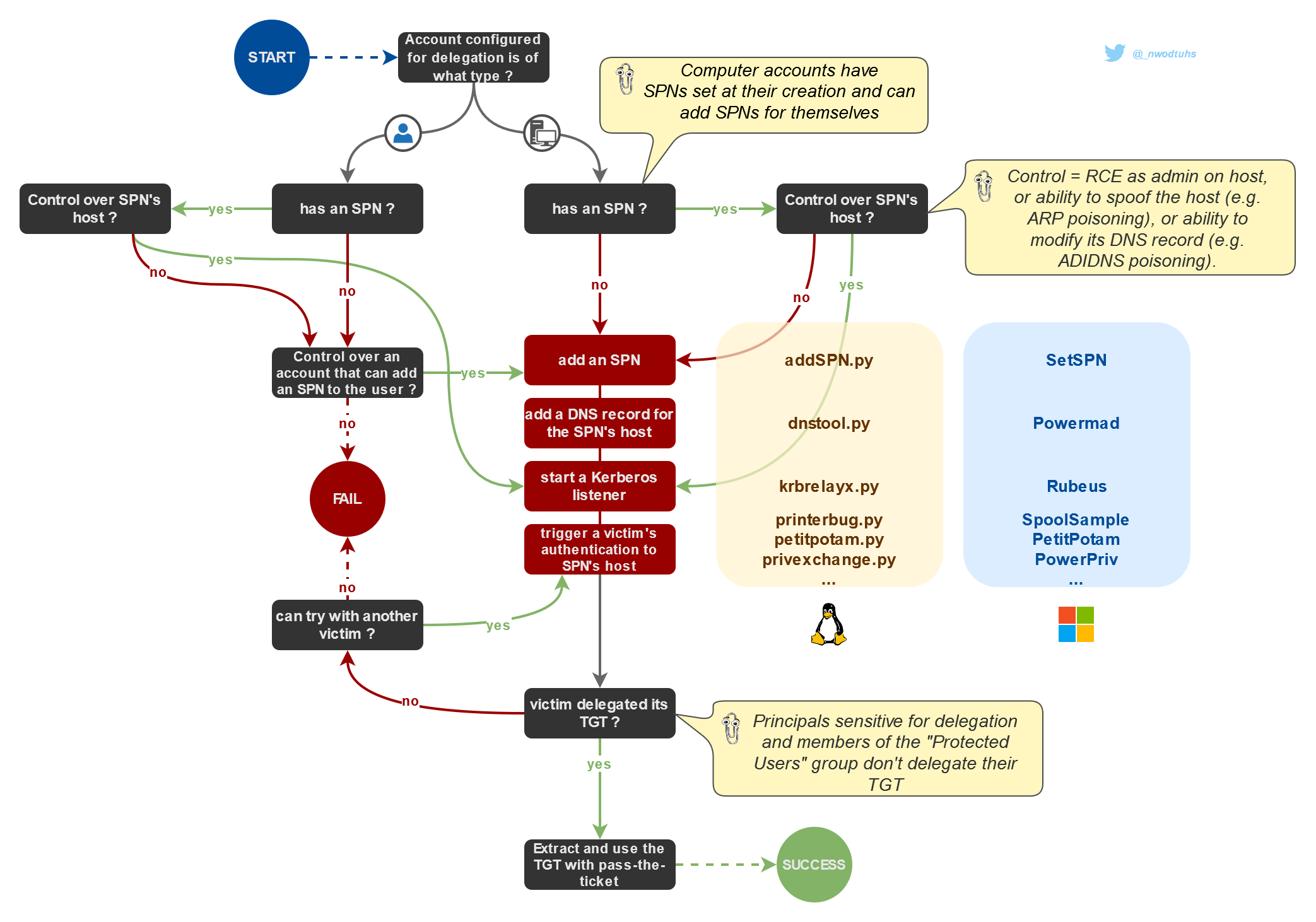
Constrained delegations (KCD)
Read the (KCD) Constrained article for more insight
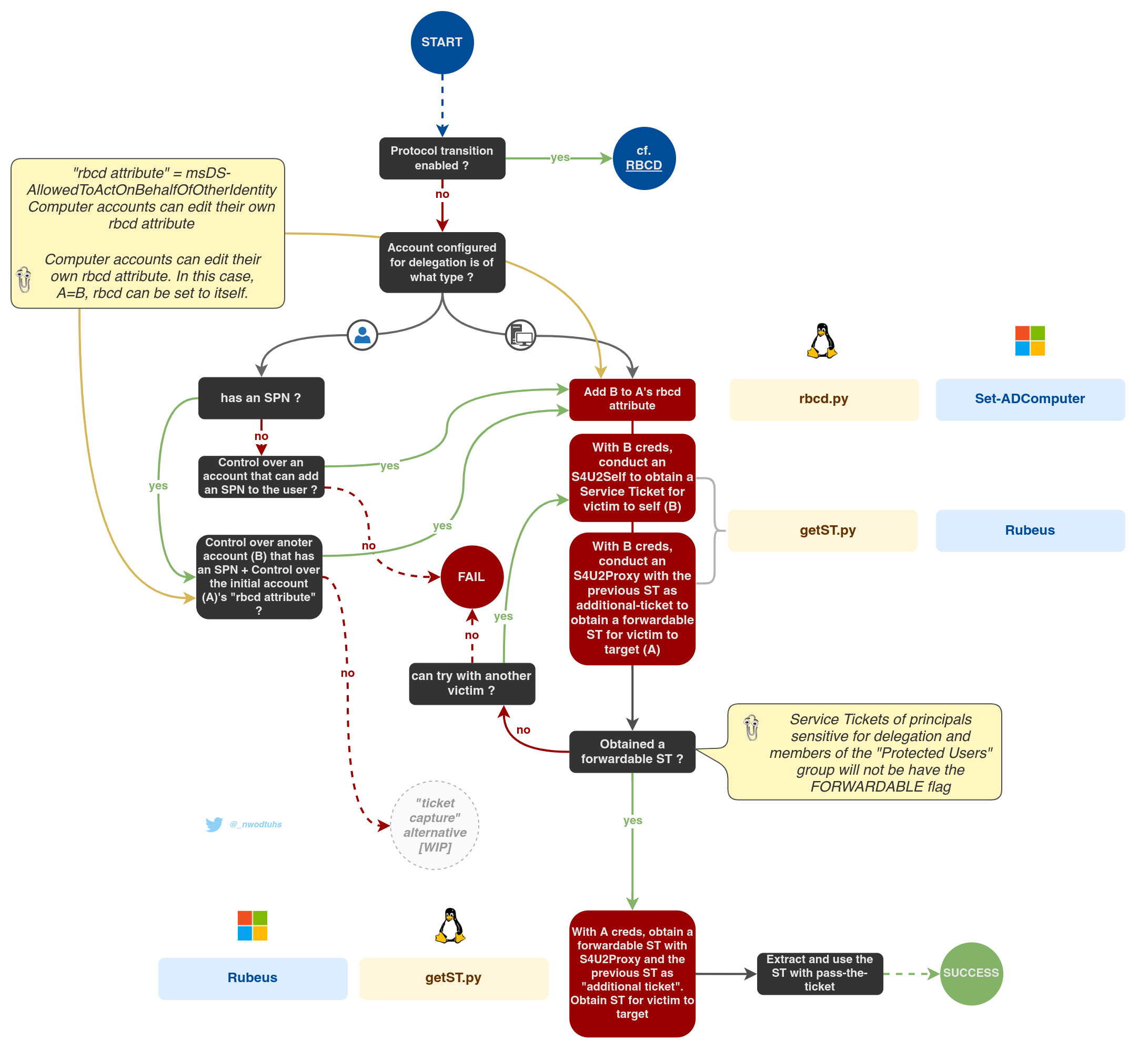
Resource-Based Constrained Delegations (RBCD)
Read the RBCD article for more insight
Talk 🎤
https://docs.google.com/presentation/d/1rAl-XKrkuFjCpExHBGrp5L8ZwtuFFrOygZMapxMp28I/edit?usp=sharing
Resources
https://blog.harmj0y.net/redteaming/another-word-on-delegation/
