🛠️ SOCKS proxy
Theory
SOCKS (SOCKet Secure) is a network protocol that allows users to route network traffic to a server on a client's behalf. SOCKS is between the application and the transport layer of the OSI model.
This is especially useful for penetration testing engagements where a target is hiding behind one or multiple firewalls. A compromised server connected to two networks can be used as a SOCKS proxy server to pivot from a network to another.
In short, a SOCKS proxy can relay TCP and UDP connections and hence help bypass network segmentation. It's sort a dynamic port forwarding technique.
Practice
There are two types of dynamic port forwarding used during penetration testing engagements.
- Dynamic port forwarding: tunnel the whole attacker's network traffic (instead of only one port) through a remote machine.
- Reverse dynamic port forwarding: tunnel the whole network traffic from a remote machine through the attacker's machine.
Basic server setup
While setting up port forwarding, it's important to remember that non-admin users can only open ports above 1024.
In practice, there are many ways to turn a controlled machine into a SOCKS proxy server.
One of the most easy is by relying on SSH, however, it requires to have an SSH server running on the controlled machine and a valid account. The tester needs to open an SSH connection to the machine that should be turned into a SOCKS proxy, and supply the -D option along with the port to use for tunneling. The command can also be used with -N option to make sure no command gets executed after the SSH session is opened.
ssh -N -D $PORT $CONTROLLED_TARGETOnce the ssh command exits successful (or once a session opens) the tester can then proceed to the usage part.
A reverse dynamic port forwarding can be also put in place to tunnel a machine's traffic through the attacker machine. It is implemented entirely in the client (i.e. the server does not need to be updated) (since OpenSSH 7.6).
ssh -N -R $PORT $CONTROLLED_TARGETBasic client usage
Once the SOCKS proxy server is set up, network traffic can be tunneled through with proxychains-ng (C), a tool still maintained and more advanced based on the original proxychains (that is not maintained anymore). The port in use by the SOCKS proxy should be supplied in the configuration file (/etc/proxychains.conf) like in the following examples.
# type ip port [user pass]
socks5 192.168.67.78 1080 lamer secret
socks4 192.168.11.49 1080
http 192.168.89.33 8080 justu hidden
http 192.168.39.93 8080Chaining proxies
In certain scenarios, SOCKS proxies can be chained. This can easily be used with proxychains. In the following example, SSH is used to turn compromised machines into SOCKS proxy servers.
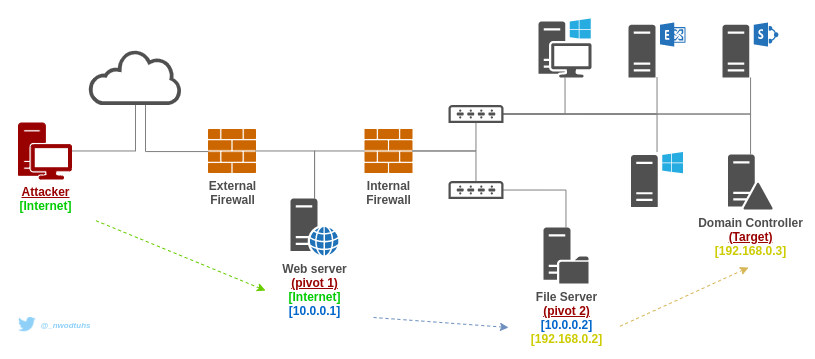
 Setting up the SOCKS proxy servers (with SSH)
Setting up the SOCKS proxy servers (with SSH)
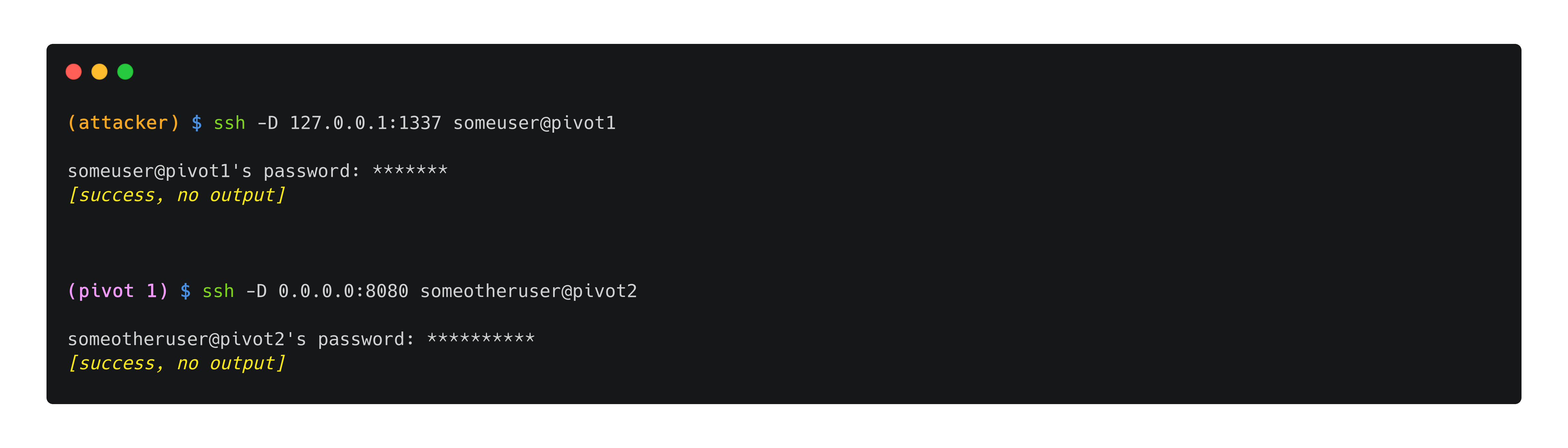
 Setting up the SOCKS proxy client (proxychains)
Setting up the SOCKS proxy client (proxychains)
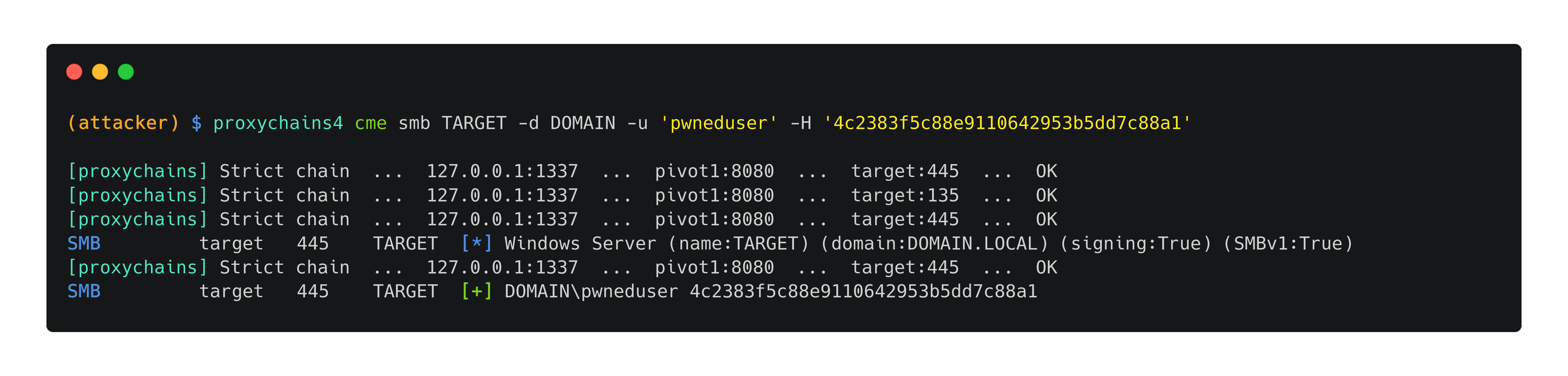 Attacking the target through the chain of SOCKS proxies
Attacking the target through the chain of SOCKS proxies
