DACL abuse
Theory
Access privileges for resources in Active Directory Domain Services are usually granted through the use of an Access Control Entry (ACE). Access Control Entries describe the allowed and denied permissions for a principal (e.g. user, computer account) in Active Directory against a securable object (user, group, computer, container, organizational unit (OU), GPO and so on)
DACLs (Active Directory Discretionary Access Control Lists) are lists made of ACEs (Access Control Entries) that identify the users and groups that are allowed or denied access on an object. SACLs (Systems Access Control Lists) define the audit and monitoring rules over a securable object.
When misconfigured, ACEs can be abused to operate lateral movement or privilege escalation within an AD domain.
Practice
If an object's (referred to as "objectA") DACL features an ACE stating that another object (referred to as "objectB") has a specific right (e.g. GenericAll) over it (i.e. over objectA), attackers need to be in control of objectB to take control of objectA. The following abuses can only be carried out when running commands as the user mentioned in the ACE (objectB) (see impersonation techniques).
Recon
DACL abuse potential paths can be identified by BloodHound from UNIX-like (using the Python ingestor bloodhound.py) and Windows (using the SharpHound ingestor) systems.
Other tools like, Get-DomainObjectAcl and Add-DomainObjectAcl from Powersploit's Powerview, Get-Acl and Set-Acl official Powershell cmdlets, or Impacket's dacledit.py script (Python) can be used in order to manually inspect an object's DACL.
Abuse
In order to navigate the notes, testers can use the mindmap below.
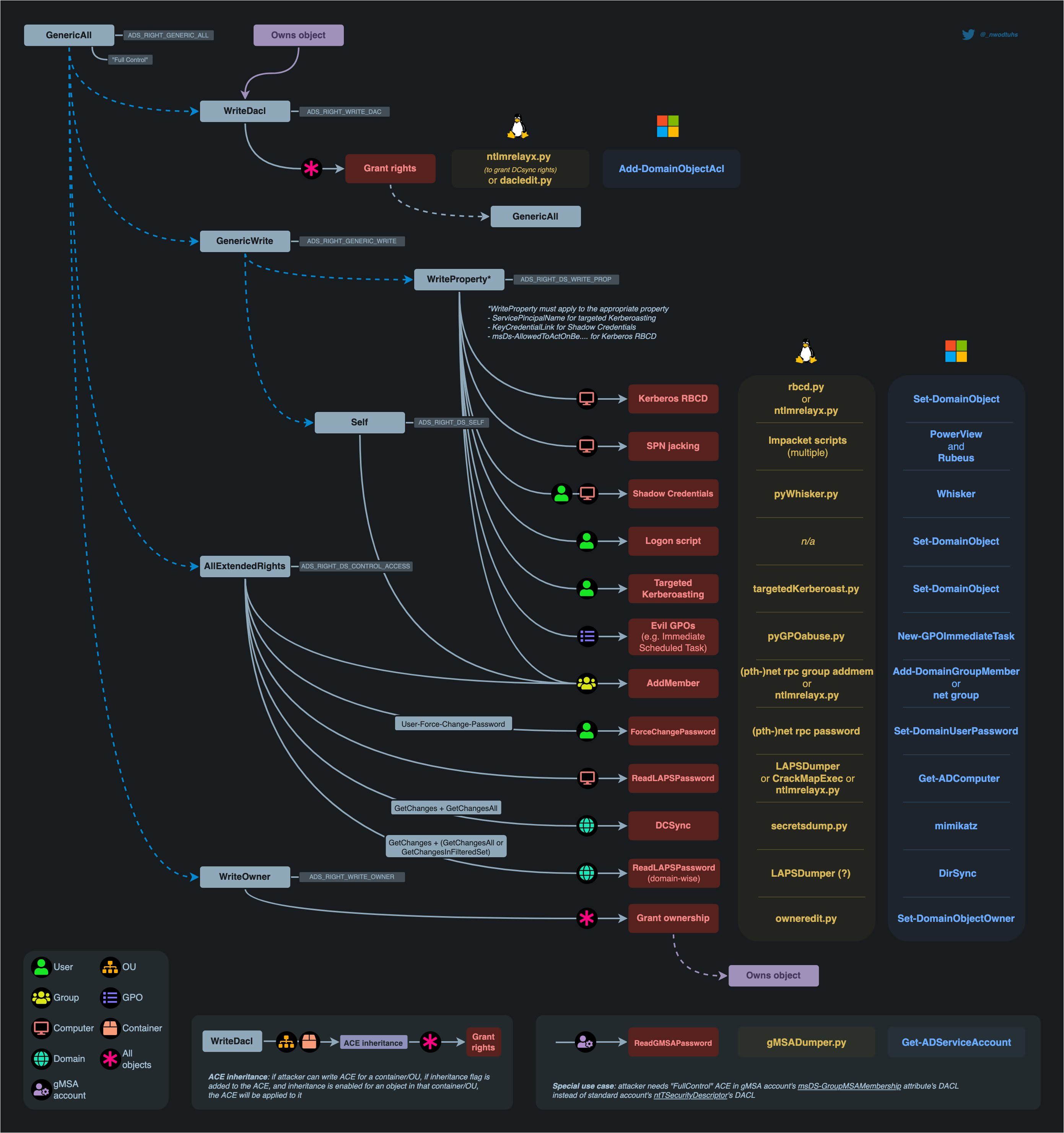
All the aforementioned attacks (red blocks) are detailed in the child notes, except:
- SPN-jacking: very specific scenario, requires lots of access: see ADDS > Movement > Kerberos > SPN-jacking
- Shadow Credentials: see ADDS > Movement > Kerberos > Shadow Credentials
- Kerberos RBCD: see ADDS > Movement > Kerberos > Kerberos Delegations > RBCD
- GPO abuses: see ADDS > Movement > GPOs
- DCSync : see ADDS > Movement > Credential > Dumping > DCSync
Self-attacks
- User and computers objects can conduct a Kerberos RCD attack on themselves.
- Computer objects can conduct a Shadow Credentials attack on themselves.
ACE inheritance
If attacker can write an ACE (WriteDacl) for a container or organisational unit (OU), if inheritance flags are added (0x01+ 0x02) to the ACE, and inheritance is enabled for an object in that container/OU, the ACE will be applied to it. By default, all the objects with AdminCount=0 will inherit ACEs from their parent container/OU.
Impacket's dacledit (Python) can be used with the -inheritance flag for that purpose (PR#1291).
adminCount=1 (gPLink spoofing)
In April 2024, Synacktiv explained that if GenericAll, GenericWrite or Manage Group Policy Links privileges are available against an Organisational Unit (OU), then it's possible to compromise its child users and computers with adminCount=1 through "gPLink spoofing".
This can be performed with OUned.py.
Disabled accounts
With enough permissions (GenericAll, GenericWrite) over a disabled object, it is possible to enable it again (e.g. set-aduser "user" -enabled 1)
BloodHound ACE edges
BloodHound has the ability to map abuse paths, with some that rely on DACL abuse. The following edges are not includes in the mindmap above:
AddKeyCredentialLink, a write permission on an object'sKey-Credential-Linkattribute, for Shadow Credentials attacksWriteSPN, a write permission on an object'sService-Principal-Nameattribute, for targeted Kerberoasting and SPN jacking attacksAddSelf, similar toAddMember. WhileAddMemberisWritePropertyaccess right on the target'sMemberattribute,AddSelfis aSelfaccess right on the target'sMemberattribute, allowing the attacker to add itself to the target group, instead of adding arbitrary principals.AddAllowedToAct, a write permission on an object'smsDS-Allowed-To-Act-On-Behalf-Of-Other-Identityattribute, for Kerberos RBCD attacksSyncLAPSPassword, bothDS-GetChangesandDS-GetChangesInFilteredSet, for synchronizing LAPS password domain-wiseWriteAccountRestrictions, which refers to theUser-Account-Restrictionsproperty set, which contains enough permissions to modify themsDS-Allowed-To-Act-On-Behalf-Of-Other-Identityattribute of the target objects, for Kerberos RBCD attacks
Permisssions index
The following table should help for better understanding of the ACE types and what they allow.
| Common name | Permission value / GUID | Permission type | Description |
|---|---|---|---|
| WriteDacl | ADS_RIGHT_WRITE_DAC | Access Right | Edit the object's DACL (i.e. "inbound" permissions). |
| GenericAll | ADS_RIGHT_GENERIC_ALL | Access Right | Combination of almost all other rights. |
| GenericWrite | ADS_RIGHT_GENERIC_WRITE | Access Right | Combination of write permissions (Self, WriteProperty) among other things. |
| WriteProperty | ADS_RIGHT_DS_WRITE_PROP | Access Right | Edit one of the object's attributes. The attribute is referenced by an "ObjectType GUID". |
| WriteOwner | ADS_RIGHT_WRITE_OWNER | Access Right | Assume the ownership of the object (i.e. new owner of the victim = attacker, cannot be set to another user).With the "SeRestorePrivilege" right it is possible to specify an arbitrary owner. |
| Self | ADS_RIGHT_DS_SELF | Access Right | Perform "Validated writes" (i.e. edit an attribute's value and have that value verified and validate by AD). The "Validated writes" is referenced by an "ObjectType GUID". |
| AllExtendedRights | ADS_RIGHT_DS_CONTROL_ACCESS | Access Right | Peform "Extended rights". "AllExtendedRights" refers to that permission being unrestricted. This right can be restricted by specifying the extended right in the "ObjectType GUID". |
| User-Force-Change-Password | 00299570-246d-11d0-a768-00aa006e0529 | Control Access Right (extended right) | Change the password of the object without having to know the previous one. |
| DS-Replication-Get-Changes | 1131f6aa-9c07-11d1-f79f-00c04fc2dcd2 | Control Access Right (extended right) | One of the two extended rights needed to operate a DCSync. |
| DS-Replication-Get-Changes-All | 1131f6ad-9c07-11d1-f79f-00c04fc2dcd2 | Control Access Right (extended right) | One of the two extended rights needed to operate a DCSync. |
| Self-Membership | bf9679c0-0de6-11d0-a285-00aa003049e2 | Validate Write | Edit the "member" attribute of the object. |
| Validated-SPN | f3a64788-5306-11d1-a9c5-0000f80367c1 | Validate Write | Edit the "servicePrincipalName" attribute of the object. |
Talk 🎤
Resources
https://docs.microsoft.com/en-us/dotnet/api/system.directoryservices.activedirectoryrights
http://www.selfadsi.org/deep-inside/ad-security-descriptors.htm
https://adsecurity.org/?p=3658
BloodHound releases
https://medium.com/@_wald0/bloodhound-1-3-the-acl-attack-path-update-74aa56c5eb3a
https://blog.cptjesus.com/posts/bloodhound20/
https://posts.specterops.io/introducing-bloodhound-3-0-c00e77ff0aa6
https://posts.specterops.io/introducing-bloodhound-4-0-the-azure-update-9b2b26c5e350
https://posts.specterops.io/introducing-bloodhound-4-1-the-three-headed-hound-be3c4a808146
https://posts.specterops.io/introducing-bloodhound-4-2-the-azure-refactor-1cff734938bd
