DC Shadow
Theory
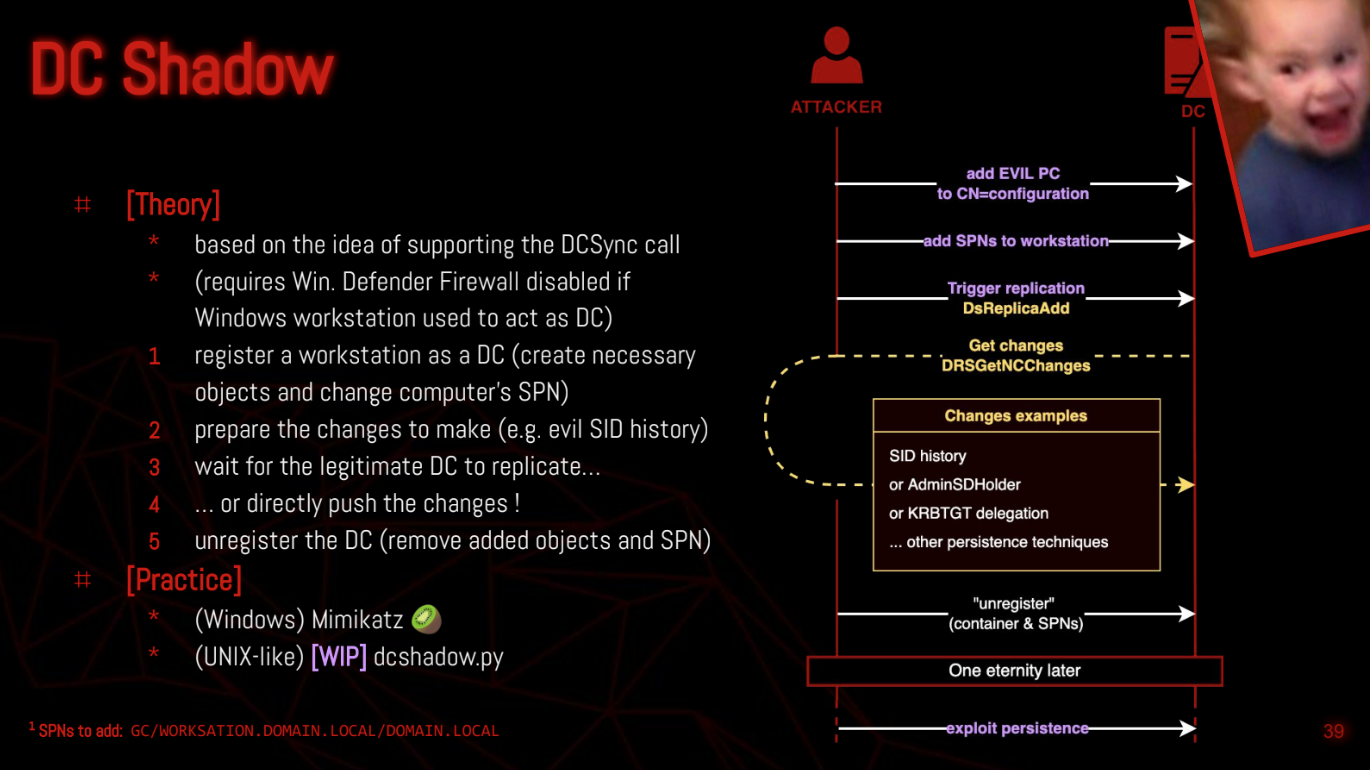
The idea behind this persistence technique is to have an attacker-controlled machine act as a domain controller (shadow DC) to push changes onto the domain by forcing other domain controllers to replicate.
There are two requirements for a machine to act as a domain controller:
- Be registered as a DC in the domain**: this is done by;
- modifying the computer's SPN (
ServicePrincipalName) toGC/$HOSTNAME.$DOMAIN/$DOMAIN - adding an entry like
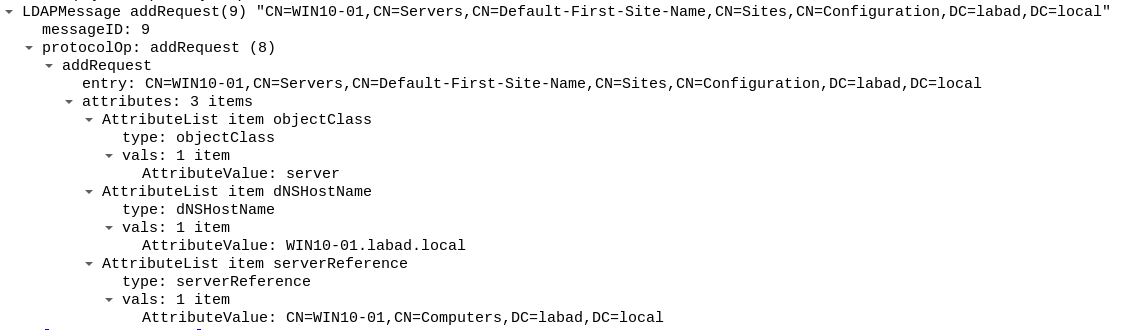
CN=$HOSTNAME,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=$DOMAINwith the following attribute values:objectClass: serverdNSHostName: $HOSTNAME.$DOMAINserverReference: CN=$HOSTNAME,CN=Computers,DC=$DOMAIN
- modifying the computer's SPN (
- Be able to request and/or respond to specific RPC calls:
DRSBind,DRSUnbind,DRSCrackNames,DRSAddEntry,DRSReplicaAdd,DRSReplicaDel,DRSGetNCChanges.
Below is the attack workflow (step 1 & 2 can be switched if need be):
- Register the workstation that will act as the shadow DC
- add the required entry in
CN=Configuration - modify the workstation's SPN
- add the required entry in
- Prepare the changes to be pushed onto the domain (with calls to
DRSAddEntry) - Push the changes by forcing another legitimate DC to replicate from the workstation with a
DRSReplicaAddcall, which automatically makes aDRSGetNCChangescall from the legitimate DC to the shadow DC. - Unregister the workstation so it is not longer considered to be a DC (by a
DRSReplicaDelcall and by reverting changes made toCN=Configurationand the workstation's SPN).
CN=Configuration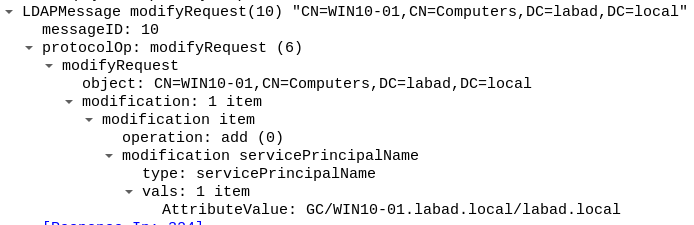
(step 1.2) modify the workstation's SPN
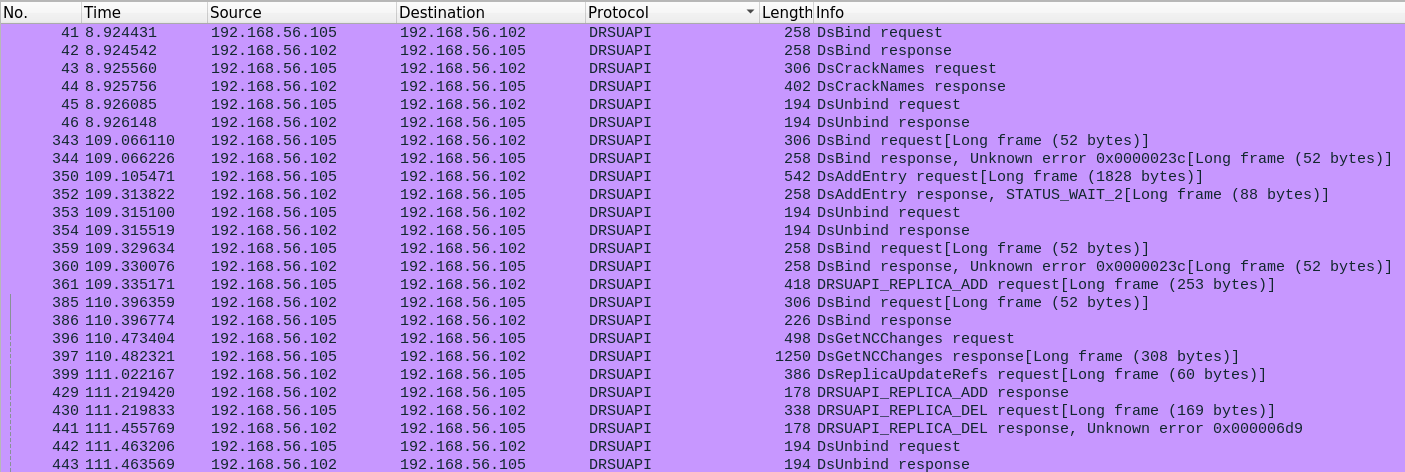
An example of DRSUAPI traffic for a successful DC Shadow attack
It is important to note that this technique can be used as a "meta" one, in the sense that it permits to use other persistence techniques, such as SID history , Delegation to KRBTGT and even DACL abuse.
For instance, a DC Shadow attack can be conducted to register a controlled workstation as a domain controller, and then use that to push changes to the domain that would expose it to DACL abuse.
"leHack 2023 - Un conseil, brûlez tout" by Charlie Bromberg and Volker Carstein"
Practice
July 27th 2023 : There is currently no way to exploit this technique purely from a distant UNIX-like machine, as it requires some tools that have yet to be made.
Talk
LeHack 2023 - Un conseil, brulez tout.pdf
Resources
https://tools.thehacker.recipes/mimikatz/modules/lsadump/dcshadow
https://stealthbits.com/blog/creating-persistence-dcshadow/
https://blog.netwrix.com/2022/09/28/dcshadow_attack/
https://www.netwrix.com/how_dcshadow_persistence_attack_works.html
